wiki:site:obecne:ipsec
Table of Contents
IPsec (Debian-Cisco) "Transportní mód"
Cisco:
crypto isakmp policy 1 encr 3des authentication pre-share group 2 lifetime 3600 crypto isakmp key YOURKEY address 10.20.30.42 no-xauth ! ! crypto ipsec transform-set hostb-transform esp-3des esp-sha-hmac mode transport ! crypto map hostb-cryptomap 1 ipsec-isakmp set peer 10.20.30.42 set transform-set hostb-transform set pfs group2 match address hostb-list ! interface FastEthernet0/1 ip address 10.20.30.40 255.255.255.0 duplex auto speed auto crypto map hostb-cryptomap ! ip access-list extended hostb-list permit ip host 10.20.30.40 host 10.20.30.42 !
# enable IKE debugging debug crypto isakmp # enable IPSec debugging debug crypto ipsec # disable all debugging no debug all
Debian:
apt-get install racoon ipsec-tools
- /etc/ipsec-tools.conf
#!/usr/sbin/setkey -f flush; spdflush; spdadd 10.20.30.42 10.20.30.40 any -P out ipsec esp/transport//require; spdadd 10.20.30.40 10.20.30.42 any -P in ipsec esp/transport//require;
- /etc/racoon/racoon.conf
path pre_shared_key "/etc/racoon/psk.txt"; path certificate "/etc/racoon/certs"; remote 10.20.30.40 { exchange_mode main; lifetime time 1 hour; proposal { encryption_algorithm 3des; hash_algorithm sha1; authentication_method pre_shared_key; dh_group 2; } } sainfo anonymous { pfs_group 2; lifetime time 1 hour; encryption_algorithm 3des; authentication_algorithm hmac_sha1; compression_algorithm deflate; }
- /etc/racoon/psk.txt
10.20.30.40 YOURKEY
/etc/init.d/setkey restart
/etc/init.d/racoon restart
# kontrola, jestli data jdou tunelem - mely by byt videt jako ESP pakety tcpdump -i eth0 # pro troubleshooting tunelu tail -f /var/log/daemon.log # spuštění racoonu v popředí v debug módu (před tím je dobré zastavit službu) racoon -d -v -F -f /etc/racoon/racoon.conf
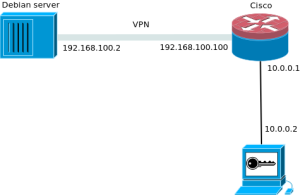
IPsec (Debian-Cisco) "Tunnel mód"
Cisco:
crypto isakmp policy 1 encr 3des authentication pre-share group 2 lifetime 3600 crypto isakmp key KEY-TEST address 192.168.100.2 no-xauth ! ! crypto ipsec transform-set TS-TEST esp-3des esp-sha-hmac ! crypto map CRYPTOMAP-TEST 1 ipsec-isakmp set peer 192.168.100.2 set transform-set TS-TEST set pfs group2 match address ACL-TEST ! interface FastEthernet0/0 ip address 192.168.100.100 255.255.255.0 duplex auto speed auto crypto map CRYPTOMAP-TEST ! interface Vlan1 ip address 10.0.0.1 255.255.255.0 ! ! ip access-list extended ACL-TEST permit ip host 10.0.0.2 host 192.168.100.2
# enable IKE debugging debug crypto isakmp # enable IPSec debugging debug crypto ipsec # disable all debugging no debug all
Debian:
apt-get install racoon ipsec-tools
- /etc/ipsec-tools.conf
flush; spdflush; spdadd 192.168.100.2/32 10.0.0.2/32 any -P out ipsec esp/tunnel/192.168.100.2-192.168.100.100/require; spdadd 10.0.0.2/32 192.168.100.2/32 any -P in ipsec esp/tunnel/192.168.100.100-192.168.100.2/require;
- /etc/racoon/racoon.conf
path pre_shared_key "/etc/racoon/psk.txt"; path certificate "/etc/racoon/certs"; remote 192.168.100.100 { exchange_mode main; lifetime time 1 hour; proposal { encryption_algorithm 3des; hash_algorithm sha1; authentication_method pre_shared_key; dh_group 2; } } sainfo address 192.168.100.2/32 any address 10.0.0.2/32 any { pfs_group 2; lifetime time 1 hour; encryption_algorithm 3des; authentication_algorithm hmac_sha1; compression_algorithm deflate; }
- /etc/racoon/psk.txt
192.168.100.100 KEY-TEST
/etc/init.d/setkey restart
/etc/init.d/racoon restart
# kontrola, jestli data jdou tunelem - mely by byt videt jako ESP pakety tcpdump -i eth0 # pro troubleshooting tunelu tail -f /var/log/daemon.log # spuštění racoonu v popředí v debug módu (před tím je dobré zastavit službu) racoon -d -v -F -f /etc/racoon/racoon.conf
wiki/site/obecne/ipsec.txt · Last modified: 2014/12/26 18:31 (external edit)